Emergency root access: Leveraging Portainer when SSH fails

In the world of DevOps, losing SSH access to your server can be a nightmare scenario. However, if you're running Portainer, there's a powerful (potentially dangerous) method for regaining root access. This article will guide you through the process of using Portainer to access a server as root when SSH is unavailable.
The power of Docker Compose
Let's start by examining a Docker Compose script that can be run through Portainer:
version: '3'
services:
busybox:
image: busybox:latest
stdin_open: true # Interactive
tty: true # TTY
volumes:
- /:/host # Bind mount / on host to /host in container
privileged: true # Run with privileged permissionsThis script creates a busybox container with the following main features
stdin_openandtty: Allows interactive shell accessvolumes: Mounts the entire host file system to /host in the containerprivileged: Grants the container full access to host features
Deploy the stack:
- Navigate to Portainer > Stacks > Create New
- Paste the Docker Compose script from above
- Click 'Deploy the stack'
Get root access:
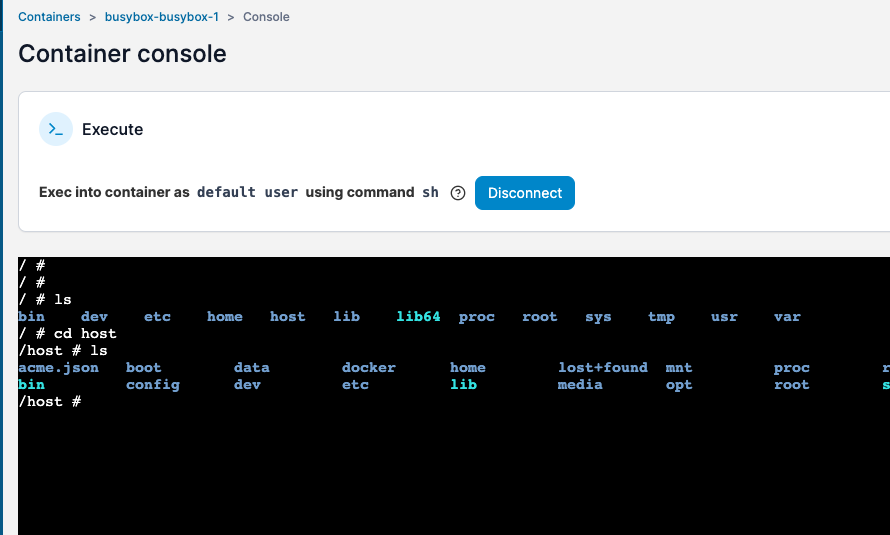
- Go to Containers > click busybox > Console > Select
/bin/sh> Connect - Type
cd hostto access the host file system - If you want: run chroot /host to become root on the host system.
The dangers of privileged access
This method grants unrestricted access to the host system, which can be extremely dangerous if misused. It's important to understand the implications and use this technique responsibly.
Security considerations
By default, Docker containers have broad access to the host system. As a result, container security is paramount. Portainer typically disables this capability for non-admin users to mitigate risks.
Practical applications
Once you have root access, you can perform critical operations such as rebooting the host (reboot now). While this method is a powerful way to regain control of your server when SSH is unavailable, it should be used with extreme caution. Always prioritize good security practices and use this technique only as a last resort.
Be secure!